
CyberKudu
Identity Management
Comprehensive identity and access management solutions that secure your digital assets while providing seamless access experiences for authorised users.
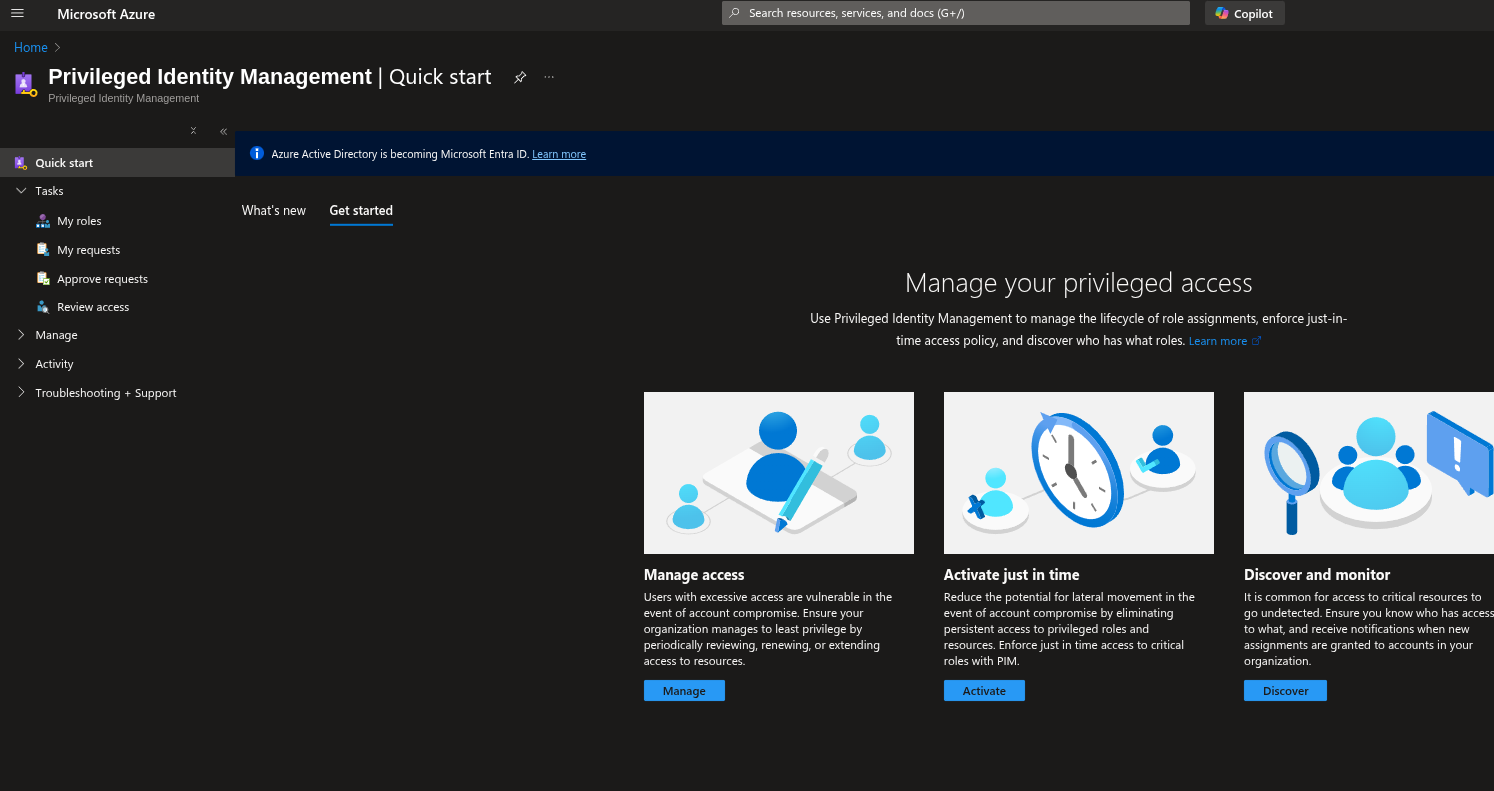
Microsoft Entra Privileged Identity Management (PIM) for just-in-time access
Microsoft Entra ID identity and access management
The Challenge
Organisations struggle to balance security with user experience when managing identities and access rights. Common challenges include managing complex user lifecycles, enforcing least privilege access, preventing credential theft, and maintaining compliance with regulatory requirements.
Key Benefits
- Protection against unauthorised access and credential theft
- Simplified user experience through single sign-on capabilities
- Improved compliance with regulatory requirements
- Reduced IT support costs related to password resets and access issues
- Enhanced visibility into who has access to what resources
Our Approach
- 1Assess your current identity management practices, identifying gaps and security risks.
- 2Design a comprehensive identity strategy aligned with security best practices and business requirements.
- 3Implement modern identity solutions including single sign-on (SSO), multi-factor authentication (MFA), and privileged access management.
- 4Establish automated user provisioning and deprovisioning workflows to manage the identity lifecycle.
- 5Develop and implement role-based access control (RBAC) to enforce least privilege principles.
Technologies & Solutions
Identity Platforms
- • Microsoft Entra ID (Azure AD)
- • Active Directory
- • Okta
- • Ping Identity
Privileged Access Management
- • Microsoft Entra Privileged Identity Management (PIM)
- • Just-in-time access
- • Privileged session management
- • Approval workflows
Authentication Solutions
- • Multi-factor authentication (MFA)
- • Passwordless authentication
- • Conditional access policies
- • Single sign-on (SSO)
Identity Governance
- • Access reviews
- • Entitlement management
- • Identity lifecycle management
- • Role-based access control (RBAC)
Outcomes
- Streamlined user access management with reduced administrative overhead
- Enhanced security through strong authentication and authorisation controls
- Improved user experience with simplified access to applications and resources
- Comprehensive audit trails for security monitoring and compliance reporting
- Reduced risk of credential-based attacks and unauthorised access
Ready to enhance your security posture?
Let's discuss how our identity management services can address your specific challenges and requirements.
Request a Consultation